TEMASOFT FileMonitor Support
We are dedicated to keeping our customers happy
We are dedicated to keeping our customers happy
For any issue or question related to TEMASOFT FileMonitor, please use the following resources. If you still don’t find an answer, please use the request form below to contact us. We will contact you back by email or by phone as soon as possible.
In order to find out more information about how certain aspects of the product work, it is a good start to check the answers to the most common questions. Click here to open the FAQ section for TEMASOFT FileMonitor.
Before investigating any issue you should check your systems against the product requirements to make sure they match. Click here to view the requirements for TEMASOFT FileMonitor.
The reference source of information of the product is always the User Manual. Click here to access the TEMASOFT FileMonitor User Manual.
If you didn’t find the answer to your problem already, click here to create a support ticket.
Expand the following items to view the answers to some of the most common questions about TEMASOFT FileMonitor.
What is TEMASOFT FileMonitor ?
TEMASOFT FileMonitor is a real-time file tracking solution delivered as on premises software, with an agent-based architecture, featuring a web-based user interface. TEMASOFT FileMonitor was designed to help users detect events related to breaches and file misuse.
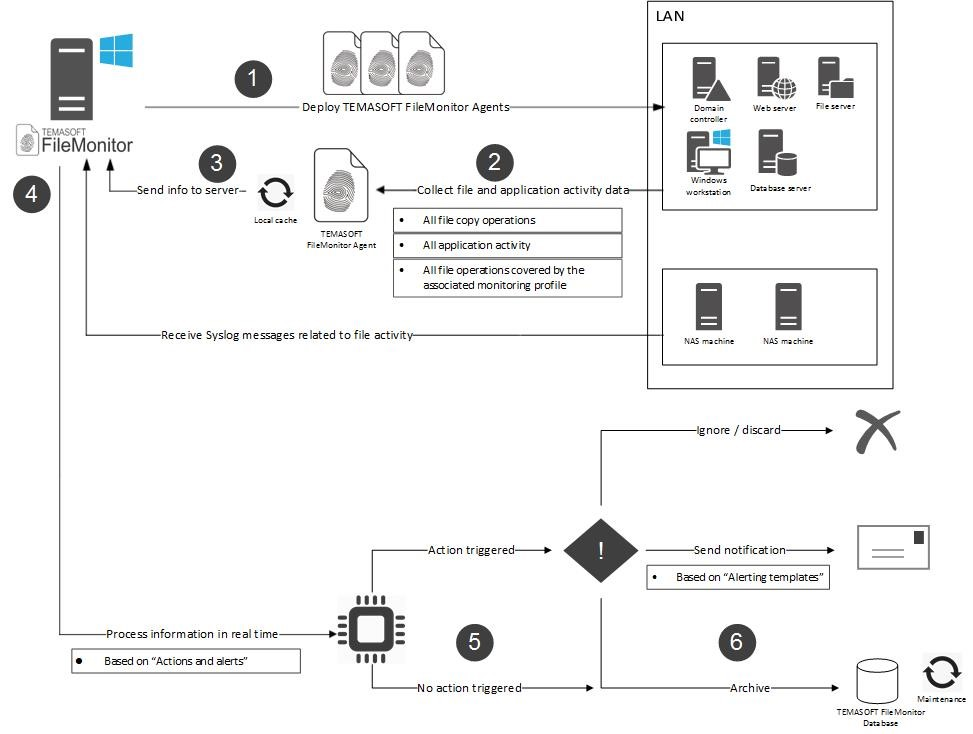
How does TEMASOFT FileMonitor work ?
TEMASOFT FileMonitor uses a Syslog receiver and agents that must be deployed on the computers to be monitored. The agents will audit file activity and send the data to the TEMASOFT FileMonitor server. The TEMASOFT FileMonitor server saves the information in an SQL Server database and features a web-based management console that provides access to the management, data analysis, reporting and alerting features.
How is TEMASOFT FileMonitor licensed ?
License file and license units
TEMASOFT FileMonitor can be used to scan different types of devices, each such device being licensed depending on the type and the operating system. These devices can be monitored using licensing units. A license file contains license units that can be assigned to the systems that need to be tracked. Clients purchase one or more license units which are typically bundled in a single license file that can be loaded in TEMASOFT FileMonitor.
Types of license keys
There are two types of license files that can be used by TEMASOFT FileMonitor:
Types of nodes
There are two types of nodes that are subject to the TEMASOFT FileMonitor licensing:
How to carry out the licensing process
TEMASOFT FileMonitor requires a license file and an internet connection to register and activate the license. This license file is received from TEMASOFT via email, either as part of the download registration process (for evaluating users) or as part of the sales process (for customers). To see the licensing status and manage the license, please follow these steps:
This window contains the license details such as licensed product version, the number of license units, the company name, license expiration date, license status (expired or not) and the number of generic and Windows workstation nodes in use and the assigned license units. To change the license, you need to click on the “load license file” button. To complete the process, you will be required a license file that is provided to you by TEMASOFT or its partners.
What actions are audited by TEMASOFT FileMonitor ?
The following actions can be audited by TEMASOFT FileMonitor:
Process related: Process creation, Process termination.
File related: File created or opened (when logged on a Windows machine, this indicates that a file has been created), File read, File write, File delete, File rename, File copy, File attributes change, File security change, File archived, File attached to Outlook, File moved to recycle bin, File restored from recycle bin, File open or create failed, File content duplicated, File probably archived (when several levels of nesting are used, it is not always possible to detect exactly which file was archived).
What information does TEMASOFT FileMonitor deliver for each audited operation ?
Essentially, TEMASOFT FileMonitor delivers information about the type of action, the user who has performed the operation, the process executable (and its path) that was used during the process, the timestamp, the file name, the destination file name (for copy, rename, etc.), the URL and browser tab page title for certain operations involving browsers, and more. For a complete list, please see the product manual.
Can TEMASOFT FileMonitor audit copy operations to network or removable devices ?
Yes, TEMASOFT FileMonitor can audit file copy operations from a monitored machine to the network, as well as file copy operations to removable storage devices. In the first case, the destination file name will contain the network path. In the second case, the operation will be flagged as “File is located on removable device”.
What special flags can TEMASOFT FileMonitor assign to file operations ?
These are the types of flags set by TEMASOFT FileMonitor:
File was read by browser: if set, together with the “File read to end” flag, it means a potential file upload via browser;
File was renamed by browser: if set, for certain files, it means a potential file download via browser;
File read to end: if set, it usually means that the whole file content was read;
User was impersonated: if set, it means that the process that generated the event impersonated the user listed under the field user name. For further forensics, please see all the available user names: process, handle, thread, etc.
File is located on removable device: if set, it means that at the time when the action occurred, the file resides on a removable device. This is useful to identify file copy operations when the destination is a removable device.
File is a directory: if set, it means that the file is a folder – used for easy monitoring of folders;
User is administrator: if set, it means that the user who caused the event has administrative privileges;
The file was changed by this operation: if set, it means that the operation resulted in a change to the file – used for easy monitoring of file changes without complex filters on the action type.
How to install TEMASOFT FileMonitor
In order to install TEMASOFT FileMonitor, please follow the below steps:
– Run the installation kit by double-clicking on the ServerInstall.exe program. The installation will unpack the necessary files;
– Installation detects any missing software prerequisites and then lists all software prerequisites and their status. Click “Install” to install any missing software prerequisites; for this step it is recommended to have an active internet connection, as some of the missing prerequisites might need to be downloaded from the internet.
– Once all the prerequisites are installed, the installer will run the product specific installation routine;
– The first dialog presents the EULA and requires you to read and accept its terms to be able to continue with the installation and to use the product. Tick the “I accept the terms of the Licensing Agreement” checkbox and click “Install” to continue;
– Next, the installation will perform the necessary operations and display the “Installation Completed” dialog. Click “Finish” to complete the installation. The “Default Configuration Wizard” will start.
The settings required for the Default Configuration Wizard differ depending on the deployment scenario. Please continue reading the deployment scenario that fits your IT environment.
How to configure TEMASOFT FileMonitor
Configuring basic settings:
Please use the Default Configuration Wizard which starts at the end of the installation process
– “Windows Service” section: please enter the credentials of a Domain Administrator, in the format DOMAIN\Username. The credentials are validated when clicking “Next”. You cannot skip this step. If the credentials are invalid, the installation will not proceed.
The Default Configuration Wizard will register the TEMASOFT FileMonitor Server Service to run under these credentials.
– “Microsoft SQL Server” section: Please select one of the existing Microsoft SQL Server™ instances. Note that the installation provides you a link from which you can install locally the Express edition of Microsoft SQL Server if no other Microsoft SQL Server™ instance is selected. Next select the type of authentication to be used. In case SQL Authentication is used, you will need to provide the SQL credentials of a user account with CREATE ANY DATABASE right. This user should also have the DB_OWNER role on every database that will be created by the product. The installer will verify if these privileges are set and will attempt to set them automatically if not already set. If Windows Authentication is used to access the database, it is recommended to use a user who is member of the Administrators group, as, by default, this group has all the necessary rights to perform the necessary database operations. The Default Configuration Wizard will verify the SQL settings before proceeding and prompt to correct any errors.
– “Web User Interface” section and subsequent steps: There is no user input required for this section and the subsequent steps. The wizard will enable IIS locally, configure it accordingly and then will deploy the necessary files for TEMASOFT FileMonitor Server. The website will run on TCP port 1753 by default.
How to deploy TEMASOFT FileMonitor agents
The next step, after having installed the TEMASOFT FileMonitor Server, is to deploy agents on the Windows computers that need to be monitored. The user interface gives you all the instructions on how to deploy Windows agents.
Configuring a monitoring profile
The monitoring profiles are very important for performing file activity auditing operations, as they instruct the TEMASOFT FileMonitor Agent, which folders and files to monitor. There can be only one monitoring profile assigned to a computer or to a group of computers. Hence, the monitoring profile must be built in such a way as to cover all the paths that are required to be monitored. TEMASOFT FileMonitor Server comes with a list of predefined monitoring profiles that cover basic use cases. You can use one of these profiles or create your own monitoring profiles. For more information, please see the product manual.
Is FileMonitor compatible with Ranstop?
Yes, the latest version of FileMonitor compatible with Ranstop builds starting with 19.9.17.5 and newer.
Expand the following items to view the system requirements for each of the TEMASOFT FileMonitor components.
TEMASOFT FileMonitor Server
TEMASOFT FileMonitor Server
Software environment:
Please note that we do not support the “Home edition” for any of the above desktop operating systems. Also, we do not support the Core editions of the server operating systems.
Hardware environment:
Minimum requirements:
Recommended:
The default ports used by the Server components are:
Firewall exclusions:
TEMASOFT FileMonitor Agent
Software environment:
Please note that we do not support the “Home edition” for any of the above desktop operating systems. We do not support Window 8 and 8.1.
Hardware environment:
Minimum requirements:
Recommended:
The Agent component only uses dynamic outbound TCP ports to connect to the Server components.
Complete the form below to report an issue. We will investigate the problem and send you an answer by email as soon as possible.