Cerber ransomware evolves to steal passwords and Bitcoin wallets
 Cerber made the headlines again, this time with the latest variant as it brings new functions to the table, highlighting the importance of enterprise ransomware protection. Some experts say that the evolution of ransomware is towards developing worm-like capabilities, like NotPetya and WannaCry, but this new Cerber variant shows another development direction: that of adapting ransomware to perform data exfiltration as well.
Cerber made the headlines again, this time with the latest variant as it brings new functions to the table, highlighting the importance of enterprise ransomware protection. Some experts say that the evolution of ransomware is towards developing worm-like capabilities, like NotPetya and WannaCry, but this new Cerber variant shows another development direction: that of adapting ransomware to perform data exfiltration as well.
So far it has been difficult to assess what happens to the data encrypted by the known ransomware variants. Most communicate with command servers and send over encrypted information. There is a possibility that victim’s data is exfiltrated to the attackers’ server, but in many cases, this has not been confirmed by experts. There is no other known ransomware implementing targeted functionality to exfiltrate data or steal certain information (like passwords).
The new Cerber variant
This new variant of Cerber ransomware, along with encrypting user files as its predecessor, also attempts to steal specific information from the target machine:
- The .dat file belonging to a few Bitcoin wallets (like Multibit): this file contains user information that can be used to access the wallets and cash out. However, the attacker also needs to hack the password to be able to use these files. So the next information attackers are after is passwords.
- Passwords stored by the popular browsers: apparently, hackers rely on the fact that users save the passwords in their favorite browser cache. Including the passwords used to access the Bitcoin wallets. So they steal all the passwords they can find in Chrome, Mozilla, and IE.
Successful attacks will provide cybercriminals with a chance to profit from the ransom paid by victims to unlock their data but will augment the earnings, if both Bitcoin wallet information and associated passwords are successfully stolen. There is a lot of information that can be taken from a user profile on a computer. The above is just an example, but attackers may target other applications or security subsystems to gain access to databases or servers based on password hashes or client applications on the victims’ machines.
General advice to avoid data theft by malware
- Always avoid saving passwords in the browsers’ caches. Browsers lead by far regarding vulnerabilities that can be exploited and the number of attacks that target them. In the case of ransomware, there is no need to hack the browser because the malicious process already runs in the security context of the user who has access to the browser’s information. So it is even easier for the attackers to get passwords, authentication cookies and other security-sensitive information that browsers manipulate;
- Purge the browsing history often, and avoid saving cookies to authenticate to websites, particularly the sites that store security-sensitive information like credit card data, personally identifiable information and so on. Such information is trivial to retrieve with a ransomware attack and can be used to access the online accounts being compromised.
- Always use lowest possible permissions and only elevate when needed. Having a standard user account with no privileges makes it difficult for ransomware to infect the machine and then to access valuable information. There is, however, ransomware able to bypass UAC and elevate privileges, so this good practice may not be 100% effective but certainly, helps with many ransomware families.
- In general, it is a good practice to avoid sacrificing security for convenience: always use strong passwords, different passwords for different websites and change them often. There are some tips available here.
Advice to avoid ransomware infections, like Cerber
The best protection against ransomware infections consists of a multilayered security strategy involving antivirus and anti-ransomware technology combined with security training to increase the awareness about how ransomware infects a machine and what to do to avoid being a victim.
Please read our article on how to protect against ransomware.
Conclusion
Cybercriminals realize that the most important trait of ransomware, its detection difficulty, can be successfully combined with old malware functionality to steal data, use the PC for malicious purposes or add worm-like capabilities for spreading horizontally. Soon, it is likely to see many such combinations where ransomware adds one or more of the capabilities above: a “WannaCry” that also steals data while spreading like a worm or a “Locky” that uses victims’ machines to carry out DDOS attacks. This is likely to be the main development direction for ransomware and the slow death of generic malware (classic computer virus), as we used to know it, three years ago.
How we can help
Our dedicated solution TEMASOFT Ranstop is an anti-ransomware software that detects present and future ransomware, based on file access pattern analysis with a high degree of accuracy. At the same time, it protects user files so that they can be restored in case of malware attacks or accidental loss. TEMASOFT Ranstop is at the core of any multi-layered security strategy designed to protect against ransomware. Learn more about how TEMSASOFT helps customers protect against Cerber ransomware.
Learn more about how TEMSASOFT helps customers protect against Cerber ransomware.
For more information, follow us on social media and subscribe to our newsletter.

Thanks for the advice! It is likely to see more ransomware attacks involving data theft.
Hi
is there a cerber decryptor ?
I received this msg from the readme file
Hi, I’am CRBR ENCRYPTOR 😉
—–
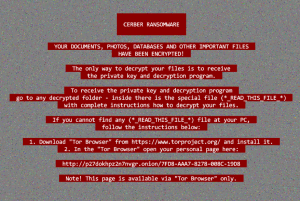
ALL YOUR DOCUMENTS, PH0T0S, DATABASES AND OTHER IMPORTANT FILES HAVE BEEN ENCRYPTED!
—–
The only one way to decrypt your files is to receive the private key and decryption program.
To receive the private key and decryption program go to any decrypted folder,
inside there is the special file (*_R_E_A_D___T_H_I_S_*) with complete instructions
how to decrypt your files.
If you cannot find any (*_R_E_A_D___T_H_I_S_*) file at your PC, follow the instructions below:
Hi Zainal,
Unfortunately, the latest versions of Cerber (v2 – out 2016) and v3 – upgraded this year, do not have a decryption tool available.
There is a decryption tool for Cerber v1, though. It is worth a try, but chances you are infected with such an old ransomware are rather slim. The tool can be found by searching for “cerber” on the NoMoreRansomware website: https://www.nomoreransom.org/en/decryption-tools.html
In general, it is best to try and prevent a ransomware incident than recover from it.
If the available tool does not work, regularly check back to NoMoreRansom website to see if there is an update.
Best regards,
Calin