TEMASOFT proudly sponsors the “2016 Insider Threat Spotlight Report.”
 The Insider Threat Spotlight report is based on a survey of more than 500 security professionals at various career levels, conducted by Crowd Research Partners in collaboration with the Information Security Community on LinkedIn. TEMASOFT is committed to supporting customers in building better data protection strategies and therefore is very interested in the latest experiences, pain-points and thoughts that security professionals have on the topic of information security and particularly on the threats from the inside. Hence, TEMASOFT is proud to have sponsored the “2016 Insider Threat Spotlight Report” and use its findings to deliver better and more useful data protection solutions.
The Insider Threat Spotlight report is based on a survey of more than 500 security professionals at various career levels, conducted by Crowd Research Partners in collaboration with the Information Security Community on LinkedIn. TEMASOFT is committed to supporting customers in building better data protection strategies and therefore is very interested in the latest experiences, pain-points and thoughts that security professionals have on the topic of information security and particularly on the threats from the inside. Hence, TEMASOFT is proud to have sponsored the “2016 Insider Threat Spotlight Report” and use its findings to deliver better and more useful data protection solutions.
Some of the key findings
74% of companies feel vulnerable to insider threats.
Less than half have proper controls in place.
Inadvertent data breaches (71 percent) top the list of insider threats companies care most about. Negligent data (68 percent) and malicious data (61 percent) breaches come in a close second and third.
Fifty-six percent of security professionals say insider threats have become more frequent in the last 12 months.
Over 75 percent of organizations estimate insider breach remediation costs could reach $500,000. Twenty-five percent believe the cost exceeds $500,000 and can reach in the millions.
For more interesting conclusions, click here to download the full report
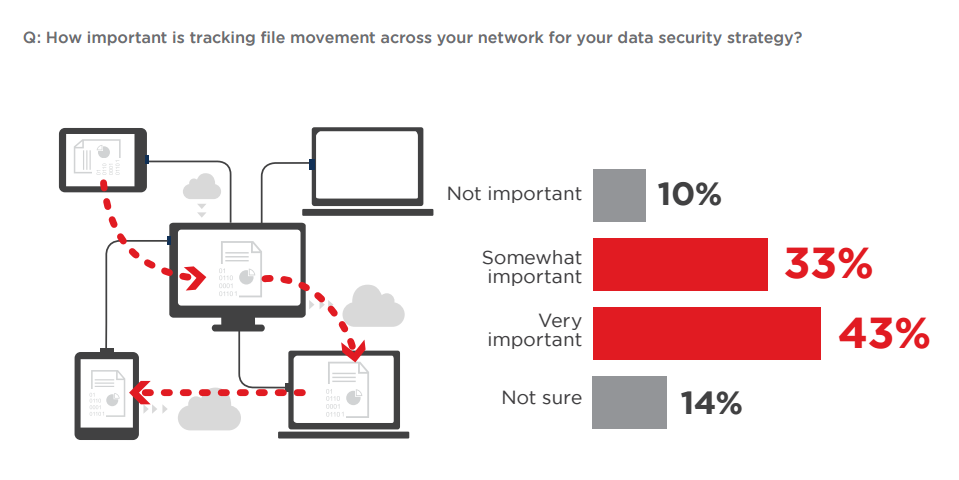
The importance of tracking file movement
TEMASOFT thought tracking file movement and complex operations is essential for a good data security strategy as it brings insight into how insiders manipulate information, detects when data is moved to hazardous locations or when insiders alter the information in ways that circumvent the data leakage prevention tools in place. This point of view has been supported by the survey results: 75 % of the respondents confirmed that tracking file movement inside the network is important for a data security strategy.
How we can help
TEMASOFT FileMonitor delivers visibility into how data moves around the network, from secure location to less secure ones or endpoints belonging to unauthorized users. Such insights are critical to extending the reach of SIEM solutions to the file auditing zone, to helping DLP solutions gain awareness on what happens on the inside, and how it may affect the perimeter, and also bring much more intelligence to behavior analysis solutions, by leveraging new file access behavior parameters. Our technology can be used to reduce the risk of data leakage, deliver file access auditing for compliance and ensure network-wide system integrity in real-time. Also, the intelligence we deliver is essential for both data breach prevention and investigation, allowing easy understanding of the relevant context, thus helping reducing the cost of data breaches.
Download the 2016 Insider “Threat Spotlight Report” here.
Liked this article? Follow us on LinkedIn for more, or subscribe to our newsletter.

