How to monitor Skype file sharing from corporate endpoints
 Skype is a popular communication platform, so companies who are concerned with data security, compliance and assessing the risk of data leakage, look for solutions that enable control and visibility into the Skype file sharing service. Knowing who shares files and which files are being shared, helps to understand the risk of data leakage and can identify data leakage incidents.
Skype is a popular communication platform, so companies who are concerned with data security, compliance and assessing the risk of data leakage, look for solutions that enable control and visibility into the Skype file sharing service. Knowing who shares files and which files are being shared, helps to understand the risk of data leakage and can identify data leakage incidents.
However, Skype is tricky to monitor because of how it works. It uses HTTP and HTTPs to communicate with peers through various types of servers, using the “Microsoft Notification Protocol”. This means that it does not connect to servers whose IPs you can filter in a firewall or network monitoring log, and monitoring all HTTP/HTTPs activity is a daunting task if you cannot filter the traffic as belonging to Skype. Blocking Skype at gateway level is also challenging as even if the generic ports are being blocked, Skype automatically reverts to dynamic ports to communicate. So, to control and monitor Skype, deep packet inspection technology is required, and, depending on desired granularity, HTTPs inspection techniques as well. Such technology would enable blocking Skype entirely, but would not allow companies only to prevent file sharing via Skype. Few advanced DLP solutions may offer functionality to prevent file sharing via Skype while allowing Skype calls and text communications, but the functionality is delivered based on complex rule-based systems that also require data categorization and are error prone, or rely on the human factor to be efficient. Monitoring which files are being shared by your users via Skype is equally challenging as file transfers are part of client-server conversations which cannot be intercepted without hacking the Skype protocol.
How Skype file sharing works
Whenever Skype uploads a file, it reads it from the source (selected by the user who wants to share the file with a peer, or a group of peers). Sometimes Skype makes a copy in a local cache, at times it only keeps the contents in the memory and starts uploading as soon as the recipient(s) accept the transfer. Taking the transfer can also occur automatically for trusted peers if so configured by the recipients.
How we can help
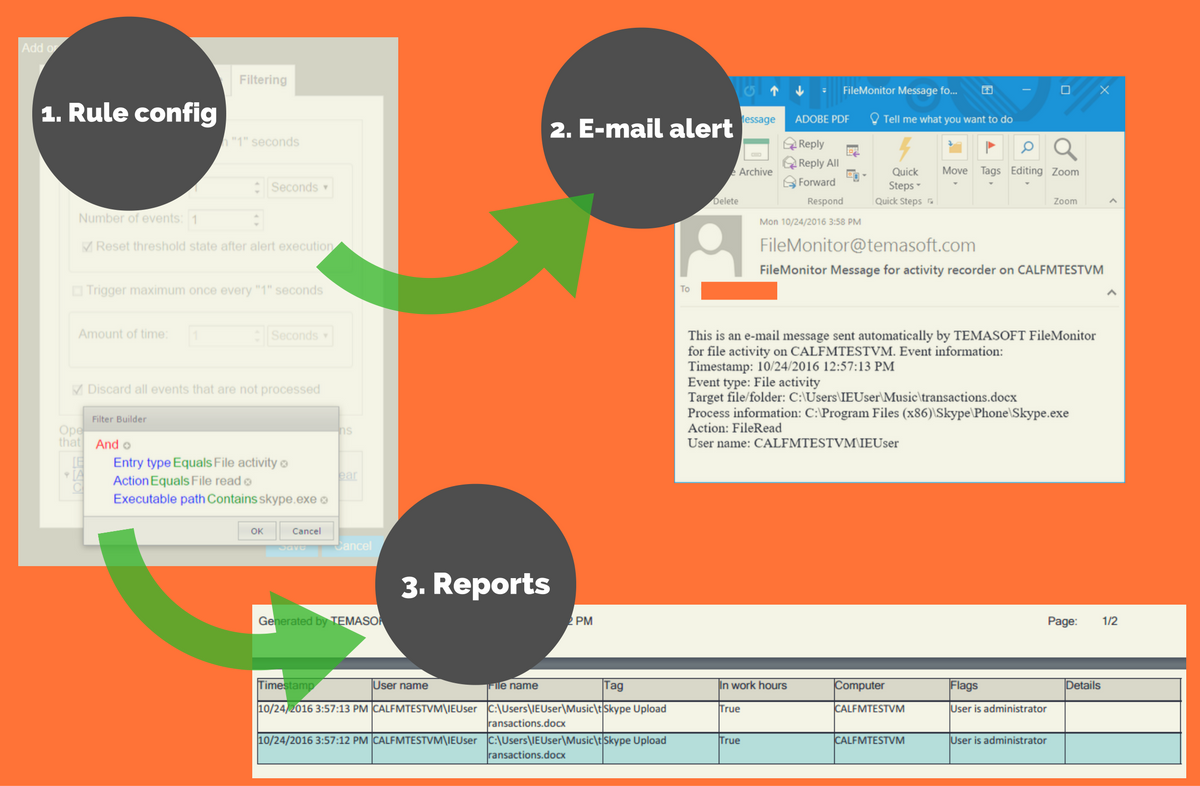
TEMASOFT FileMonitor audits file access patterns and can identify file activity performed by the Skype process. The Skype process itself should not read anything from the hard drive, except particular configuration files, local cache, and resources like images, emoticons, etc. No way should it read .docx or .PDF files unless those files are being shared. TEMASOFT offers an easy way to monitor Skype file sharing activity based on how files are being accessed. To do that, a TEMASOFT FileMonitor Agent needs to be active on the endpoint where Skype runs:
- First, configure TEMASOFT FileMonitor Server to tag files being read by the Skype process, which also have particular file types (such as documents);
- Next, make sure the rule runs on the server too, and configure the email settings to receive an email alert when a file is shared via Skype;
- Once these are set up, you can watch the Skype file sharing activity in the Data Viewer by just adding the “Tag” column, and entering “Skype” in the associated filter box (while making sure that the operator is set to “contains”);
- The “Tag” field containing “Skype upload” or whatever tag name was configured with the rule, can also be used as filtering criteria for reports. Once set, you can run the reports manually or schedule them on a daily basis (and receive the reports in your mailbox).
Next, you can further enhance the filters of the rule, to include or exclude events, depending on any parameter. TEMASOFT FileMonitor allows configuration granularity that enables IT admins to reduce noise by filtering out files commonly read by Skype. At the same time, further filtering allows only tagging and alerting on files marked as sensitive (by other rules), or if the activity is marked as suspicious (i.e. because it occurs outside normal operational time).
This monitoring functionality is delivered by TEMASOFT FileMonitor silently, so your users may not be aware that their file sharing activities are monitored. In some countries, the law requires that employees are made aware when their activities are being monitored. Only making employees aware of this fact significantly reduces the file sharing activity.
Conclusion
The new version of TEMASOFT FileMonitor offers critical details to understand how Skype file sharing is used by companies, hence it helps reduce the risk of data leakage by keeping IT administrators informed and also helps consolidate data security strategies. We will present ways for monitoring other file sharing services in upcoming blog posts, so please follow us if you are interested in finding out more.
For more information about the next version of TEMASOFT FileMonitor and how it can also track other file sharing services like Dropbox or One Cloud, follow us on LinkedIn or subscribe to our newsletter.