Data breach statistics for H1 of July 2016: Insider vs. ransomware
The first two weeks of July were rich in data breaches, especially in the healthcare sector. According to official reports in the US, a number of 17 breaches were reported, the large majority, affecting healthcare organizations, where all data breaches affected more than 500 individuals, hence, falling under the requirements of section 13402(e)(4) of the HITECH Act. In all, healthcare organizations in the US lost 48.246 records during the first half of July 2016.
 |
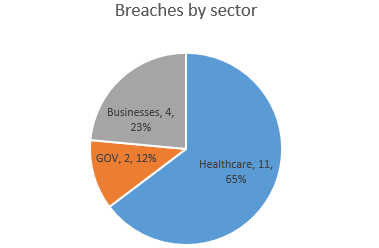 |
The most affected entities were Dr. Q Pain and Spine d/b/a Arkansas Spine and Pain losing 17,100 records and The Ambulatory Surgery Center at St. Mary, losing 13,000 records – both breaches occurred because of a hacking / IT incident involving network servers.
The data loss at The Ambulatory Surgery Center at St. Mary is of particular interest as ransomware played an important role. Hackers installed ransomware on the server and demanded ransom for data recovery. The ransomware attack was not detected until employees have observed encrypted files and reported the incident. Investigation in this case is still ongoing and it is not clear how hackers managed to get access, but according to official reports, the entity had backups and no ransom was payed. However, since the ransomware read the files before encrypting, there is no way of telling if that information was forwarded or not to hackers’ command centers, given the current auditing means in place. This attack proves once again that ransomware does not cause only data loss and downtime, but also triggers data breaches which need to be reported and investigated, adding to the cost of the incidents. With ransomware emerging as the main threat to data nowadays, it is clear that the risk of such incidents occurring can only be mitigated by using layered approaches to data security that involves training, auditing access to data, malware detection working together with accurate ransomware detection tools.
Another interesting incident involved the insider and occurred at Providence Medical Group- Gateway Clinics – 5,400 affected records, where, during an internal audit, it was found that an employee had been accessing patient record files for almost 4 years. The unauthorized insider had access to medical treatment information and presumably to insurance information and social security numbers as well. This incident shows how trivial it is to lose track of which data is accessed and by whom, when not focusing enough on data security. The amount of time data was at risk in this case, without anybody noticing, is simply amazing. In this case, simple data access auditing with alerting functionality would have helped the organization identify the unauthorized access very early and most probably prevent the data breach.
Data sources used in this article:
U.S. Department of Health and Human Services Office for Civil Rights www.hhs.gov;
Privacy Rights Clearinghouse: www.privacyrights.org;
Liked this article? Follow us on LinkedIn for more, or subscribe to our newsletter.
