28 Years of Cyber Extortion: From Floppy Disk to Cloud
 Cyber extortion has been around for nearly three decades, and the general feeling you get when reading the news nowadays is that the world is not yet prepared to deal with it. Although sustained efforts have been made to combat ransomware, the primary tool for cyber extortion, many businesses and institutions still fall victim to attacks on a regular basis, with frightening ease.
Cyber extortion has been around for nearly three decades, and the general feeling you get when reading the news nowadays is that the world is not yet prepared to deal with it. Although sustained efforts have been made to combat ransomware, the primary tool for cyber extortion, many businesses and institutions still fall victim to attacks on a regular basis, with frightening ease.
It all began with a floppy disk in an envelope
We are in 1989, when the Internet is still an experiment in linking together several large networks. Scientists are still adopting protocols and figuring out how to connect their own networks to others’. The World Wide Web is about to be born, and Intel is announcing its 486 processors. Compaq is selling computers with 1MB of RAM starting at $2,600, while IBM is selling a 20-pound machine with a 60MB hard drive for over $7,600. There are few people using computers but that doesn’t stop the developer of the first cyber extortion program.
Ironically, the first example of ransomware is written by a biologist, not by a programmer, and it is distributed via mail, in an envelope containing a floppy disk and a letter. The AIDS epidemic is in full swing, so the letter claims that the diskette contains a survey for assessing the patient’s risk of contracting AIDS. However, it also contains a Trojan that lays dormant for a while and then hides the folders on the hard drive and encrypts all the file names. It then asks for $189, to be sent to a PO box in Panama, in exchange for restoring access to data.
Several years from now, two cryptographers (Young and Yung) will research a version of ransomware using asymmetrical encryption and will be the first to write about the possibility of extorting electronic money via encryption, coming up with the concept of cyber extortion.
The first ransomware was mailed on a floppy disk and asked for the ransom to be paid to a PO box in Panama.
Ransomware evolves:
features, distribution, and monetization
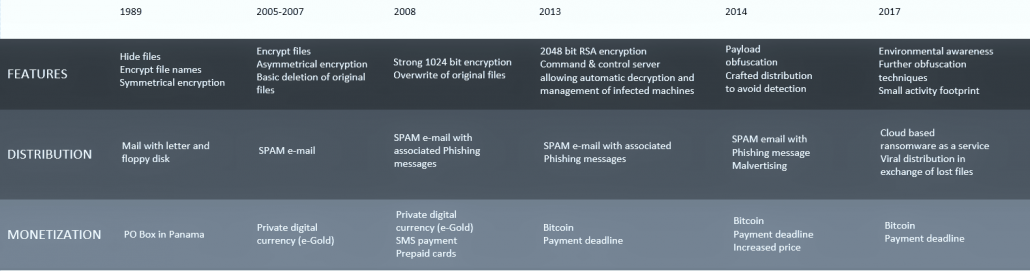
Early days: 1989–2011
The first ransomware featured symmetrical encryption of file names and the ability to hide files on a hard disk (AIDS Trojan, 1989), but by 2005 it had become capable of encrypting actual data (Gpcode) with asymmetrical encryption and had much stronger keys, up to 1024-bit—enough to be unbreakable. Along with encryption, the methods for disposing of the original files also evolved from common deletion—so they were recoverable with specialized tools—to secure deletion and overwriting of associated disk sectors (Gpcode.AK, 2008).
As Internet use spread, email became the preferred distribution model thanks to its fast delivery and broad reach.
Before the widespread availability of electronic payment, ransom money was received in anonymous PO boxes in countries without little financial or criminal control. As private electronic currencies such as E-Gold appeared, they were adopted as preferred payment methods.
Maturity: 2012–2014
Encryption strength grew to 2048-bit, and functionality was added to allow remote control and management of infected machines via command and control servers. CryptoLocker was the first ransomware to introduce this technology, in 2013 . Primary obfuscation methods, such as hiding malicious code, allowed the malware to evade payload detection by antivirus programs such as hiding the malicious code as it executes (internal obfuscation). CryptoWall first introduced this technology, in 2014, challenging existing security solutions.
Perpetrators of cyber extortion also improved their use of email as a distribution model, crafting the content of email messages, developing phishing techniques to lure users into opening infected attachments, and impersonating legitimate authorities or companies. Ransomware also started spreading via malvertising campaigns and clickbait from malicious websites pretending to deliver free copyrighted content such as movies, music, and software.
New monetization methods appeared, including payment via SMS to premium numbers, prepaid cash services, and the use of electronic currency.
Next-gen ransomware: 2014 and beyond
The obfuscation and evasion techniques have become very advanced, with new ways of hiding malicious code, the ability to detect sandbox and virtual environments, and functionality to confuse automated security tools like signature-based detection, the creation of firewalls blocking traffic to command and control servers, and so on.
The most significant development in the distribution model has been its availability as a cloud-based service, within the TOR network, for example. For more on this, read our blog article . This allows even nontechnical people to become ransomware attackers for a slight fee or a portion of the ransom profits. The release of Popcorn Time at the end of 2016 was another milestone: this ransomware promises to return your data if you pass the virus along to other victims (read more here), leading to a highly reliable distribution. For more on this, read our blog article.
The introduction of Bitcoin made things very easy for ransomware attackers because of the anonymity it provides as well as its popularity and ease of use. Billions of dollars in Bitcoin are now being extorted by cyber criminals through ransomware and other means.
The future of ransomware
Functionality intended to render files unusable has more or less reached a cap, so ransomware creators are now likely to focus more on payload execution. High volumes of variants, some with dummy functionality, confuse security researchers and delay the reactions of security solutions, allowing a wider “zero day” effectiveness of primary ransomware strains. High-profile targets are likely to get attacked with custom, dedicated ransomware strains for increased effectiveness, and social engineering will play a significant role in distributing malicious content.
With the need now to synchronize across platforms, new ransomware distribution models will target mobile devices and replicate on computers. Future ransomware will likely expand its mission from taking files hostage to performing other malicious activities, such as disabling a business or public service. With the growth of smart offices featuring automated access points, elevators, power supplies, and communication networks, the avenues for cyber extortion grow immensely.
The fast evolution of distribution channels due to the prevalence of cloud computing increases the number of potential attackers and the number of attacks. New ransomware features make it very challenging for companies to protect against attacks, and the availability of Bitcoin provides an easy way to monetize malicious activity. These factors ensure that ransomware will remain one of the greatest threats to IT security.
Follow us on Twitter and subscribe to our newsletter to stay abreast of the latest on ransomware and protect yourself against it.